Threat Actors Are Exploiting Vulnerabilities Faster: What You Need to Know
Threat Actors Are Exploiting Vulnerabilities Faster: What You Need to Know
In today's rapidly evolving threat landscape, cybercriminals are becoming increasingly adept at exploiting vulnerabilities in software and systems. What was once a race against the clock measured in weeks or months has now shrunk to days, or even hours. This accelerated exploitation timeline demands a proactive and vigilant approach to cybersecurity.

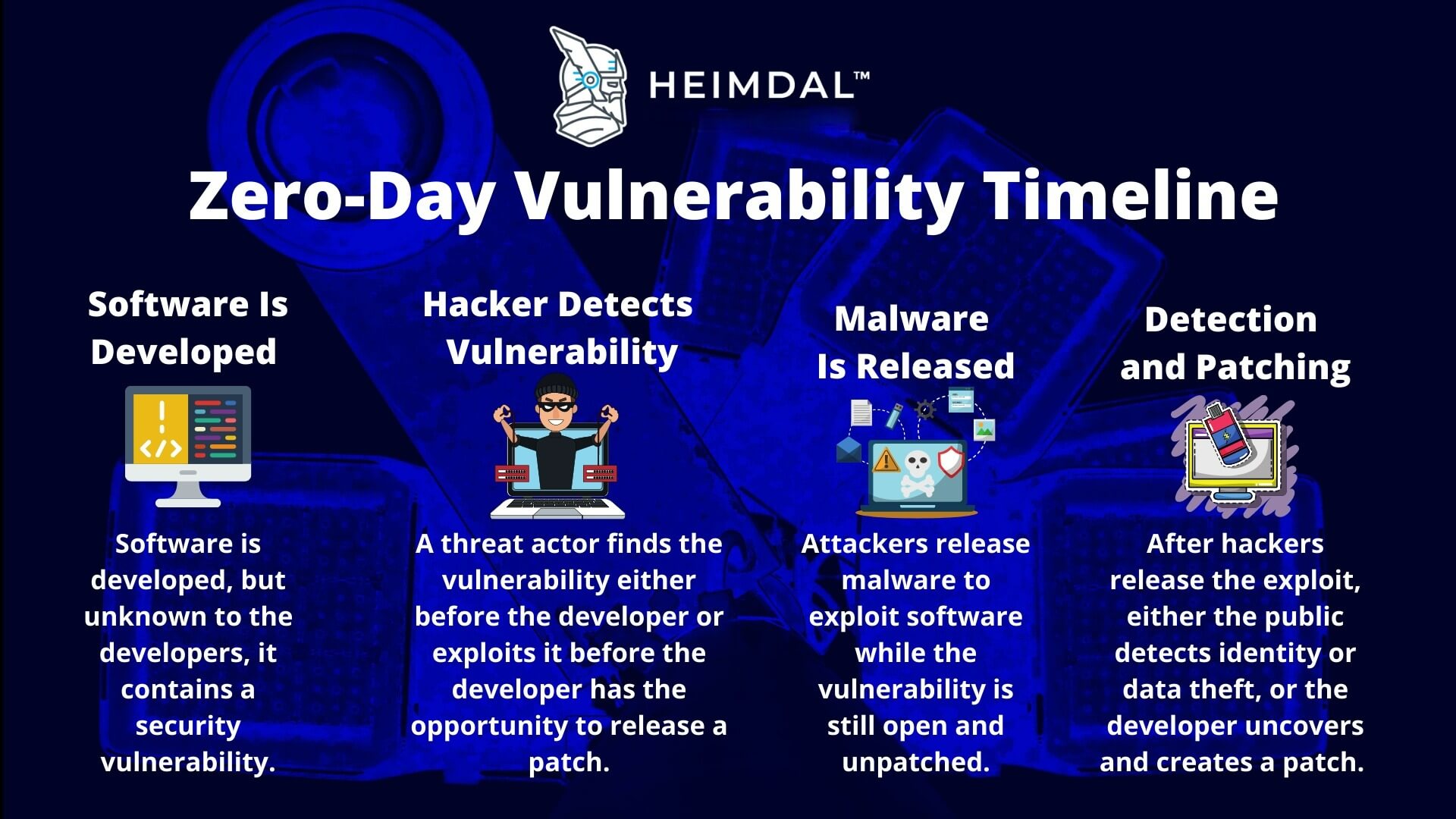
A Quick Guide to Zero Day Attacks, Exploits, and Vulnerabilities
The Shrinking Window of Opportunity
Reports indicate a significant decrease in the time it takes for threat actors to weaponize and exploit newly discovered vulnerabilities. This means organizations have less time to patch their systems and mitigate potential risks. The rise of zero-day exploits, where vulnerabilities are exploited before a patch is available, further exacerbates this challenge.
According to a recent VulnCheck report, a significant percentage of vulnerabilities are now being exploited within days of being added to the Known Exploited Vulnerabilities (KEV) catalog. This rapid exploitation necessitates a shift from reactive patching to proactive threat hunting and vulnerability management.
Recent Examples of Accelerated Exploitation
Several recent incidents highlight the speed at which threat actors are now operating:
- Microsoft SharePoint Vulnerabilities: In July 2025, multiple vulnerabilities in on-premises Microsoft SharePoint servers (e.g., CVE-2025-49704, CVE-2025-49706, CVE-2025-53770) were actively exploited, allowing attackers to achieve remote code execution.
- Niagara Framework Flaws: Critical vulnerabilities in the Niagara Framework, which is used in smart buildings and industrial systems, were recently discovered. Attackers chained CVE-2025-3943 and CVE-2025-3944 to gain root-level remote code execution.
Protecting Your Organization
To defend against these rapidly evolving threats, organizations should implement the following measures:
- Timely Patching: Prioritize patching known vulnerabilities as soon as updates are available. Implement a robust patch management process to ensure timely deployment.
- Vulnerability Scanning: Regularly scan your systems for vulnerabilities using automated tools. Identify and remediate any weaknesses before they can be exploited.
- Threat Intelligence: Stay informed about the latest threats and vulnerabilities by subscribing to threat intelligence feeds and security advisories.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to detect and respond to malicious activity on your endpoints.
- Security Awareness Training: Educate your employees about phishing and other social engineering tactics. Human error remains a significant factor in many successful cyberattacks.
- Zero Trust Architecture: Implement a zero-trust security model, which assumes that no user or device is trusted by default. Verify every access request before granting access to resources.
Key Takeaways
The speed of vulnerability exploitation is increasing, making it crucial for organizations to adopt a proactive security posture. By prioritizing timely patching, vulnerability scanning, threat intelligence, and security awareness training, you can significantly reduce your risk of falling victim to cyberattacks. Staying informed and vigilant is essential in today's dynamic threat landscape.
References
- https://heimdalsecurity.com/blog/wp-content/uploads/Zero-Day-Vulnerability-Timeline.png.jpg
- https://www.vulncheck.com/blog/state-of-exploitation-1h-2025
- https://unit42.paloaltonetworks.com/microsoft-sharepoint-cve-2025-49704-cve-2025-49706-cve-2025-53770/
- https://blog.checkpoint.com/research/sharepoint-zero-day-cve-2025-53770-actively-exploited-what-security-teams-need-to-know
- https://thehackernews.com/2025/07/critical-flaws-in-niagara-framework.html





