PXA Stealer: New Python Malware Breaches 200,000 Passwords via Telegram

PXA Stealer: New Python Malware Breaches 200,000 Passwords via Telegram
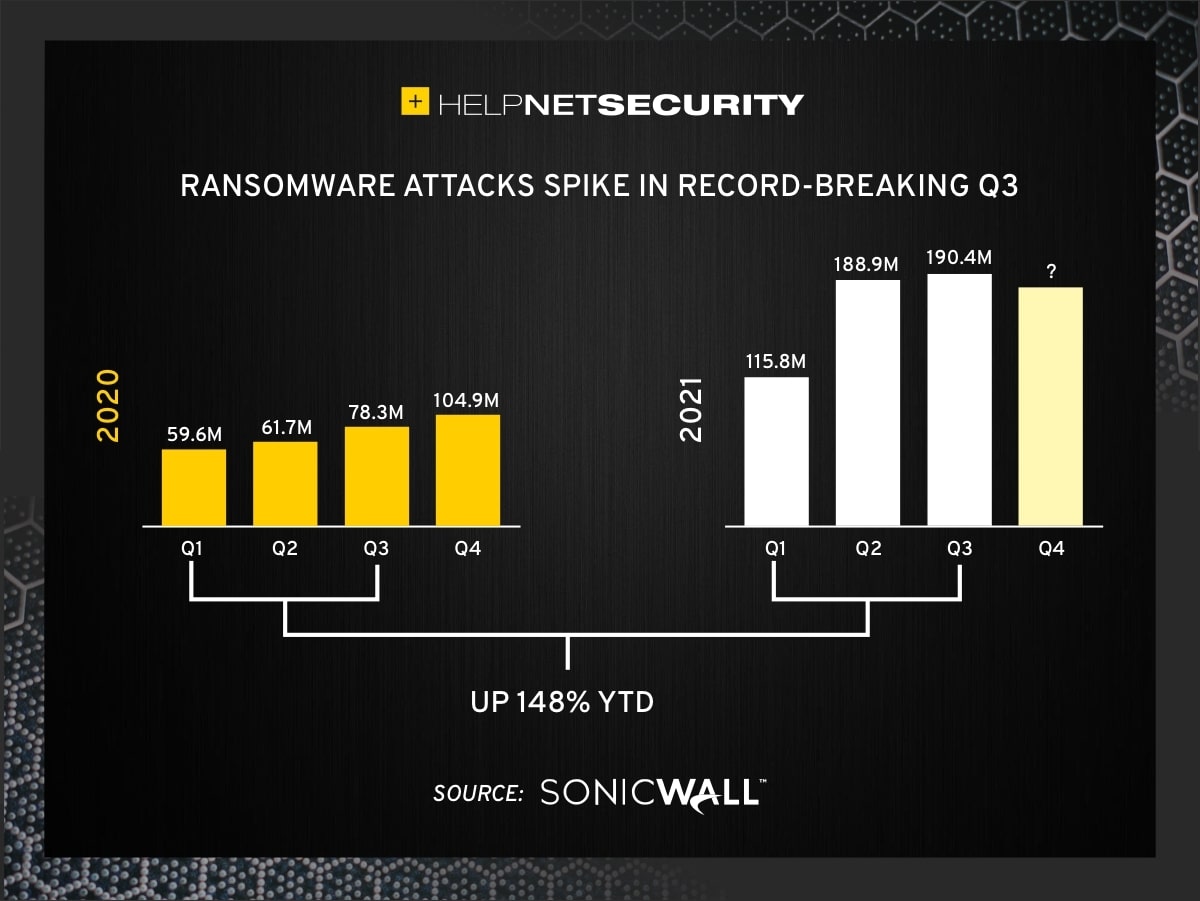
A new information stealer, dubbed PXA Stealer, has emerged as a significant threat, compromising over 200,000 unique passwords and numerous credit card details. This Python-based malware is being distributed through Telegram channels, posing a serious risk to unsuspecting users. Understanding how PXA Stealer operates and taking proactive steps to protect your data is now more critical than ever.

Top Data Breaches in 2023: Alarming Incidents Impacting Companies
What is PXA Stealer?
PXA Stealer is a Python-based information stealer designed to harvest sensitive data from infected systems. Cybersecurity researchers have recently uncovered a surge in campaigns leveraging this malware, particularly targeting users through Telegram channels. The stealer is capable of extracting a wide range of information, including:
- Passwords stored in web browsers
- Credit card details
- Data from VPN clients
- Cloud command-line interface (CLI) utilities
- Information from connected fileshares
- Data from applications like Discord
How Does it Spread?
The primary distribution method for PXA Stealer is through malicious archive files disguised as PNG or PDF documents. These files are often bundled with decoy files to distract users and analysts. The malicious archives sideload PXA Stealer through a complex execution chain, ultimately leading to the compromise of the victim's system. The stealer uses BotIDs (stored as TOKEN_BOT) to establish a link between the main bot and various ChatIDs (stored as CHAT_ID), facilitating data exfiltration via Telegram.
Who is Behind It?
While attribution is always challenging, evidence suggests that Vietnamese hackers are actively involved in developing and deploying PXA Stealer. The operation, sometimes referred to as "Ghost in the Zip," highlights an evolving ecosystem where stealers are continuously refined and distributed.
How to Protect Yourself
Protecting yourself from information stealers like PXA Stealer requires a multi-faceted approach:
- Be cautious of suspicious files: Avoid opening archive files (ZIP, RAR, etc.) received through untrusted sources, especially on Telegram.
- Verify file extensions: Double-check the actual file extension. A file named "document.pdf.exe" is likely an executable, not a PDF.
- Keep software updated: Regularly update your operating system, web browsers, and other software to patch security vulnerabilities.
- Use strong, unique passwords: Employ a password manager to generate and store strong, unique passwords for each of your online accounts.
- Enable multi-factor authentication (MFA): Whenever possible, enable MFA to add an extra layer of security to your accounts.
- Install a reputable antivirus program: A good antivirus program can detect and block malware before it can infect your system.
- Be wary of phishing attempts: Phishing emails and messages can trick you into revealing sensitive information or downloading malicious files.
Key Takeaways
The PXA Stealer represents a significant threat to online security, highlighting the importance of vigilance and proactive security measures. By understanding how this malware operates and following the recommended सुरक्षा practices, you can significantly reduce your risk of becoming a victim.
References
- The Hacker News: Vietnamese Hackers Use PXA Stealer, Hit 4,000 IPs and Steal 200,000 Passwords Globally
- Infosecurity Magazine: Ghost in the Zip Reveals Expanding Ecosystem Behind PXA Stealer
- SentinelOne: Ghost in the Zip | New PXA Stealer and Its Telegram-Powered Ecosystem
- Heimdal Security: Top Data Breaches in 2023: Alarming Incidents Impacting Companies