Akira Ransomware Exploits SonicWall Zero-Day: What You Need to Know
Akira Ransomware Exploits SonicWall Zero-Day: What You Need to Know
A surge of Akira ransomware attacks is currently targeting SonicWall firewall devices, potentially exploiting a previously unknown security vulnerability. This poses a significant threat to organizations using these devices, demanding immediate attention and proactive measures.

SonicWall firewall devices are being targeted by Akira ransomware.
What is the Akira Ransomware?
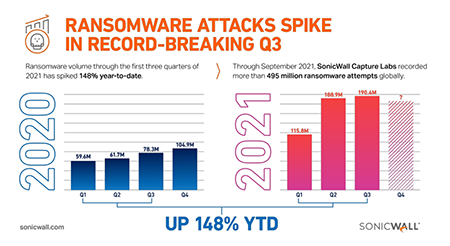
Akira is a ransomware group that has been active since early 2024. They are known for targeting various organizations and have reportedly extorted approximately $42 million from over 250 victims. The group employs a double-extortion strategy, encrypting data and threatening to leak it publicly if the ransom is not paid. Recently, they have focused their attacks on SonicWall SSL VPNs, indicating a shift in their tactics.
The SonicWall Vulnerability
The recent wave of attacks suggests the exploitation of a zero-day vulnerability in SonicWall firewalls. While the exact nature of the vulnerability is still under investigation, some reports point to a potential improper access control flaw (possibly CVE-2024-40766) in SonicOS affecting Gen 5 devices. This vulnerability allows attackers to gain unauthorized access to the firewall and deploy the Akira ransomware.
Which SonicWall Products Are Affected?
While the specific models affected are still being investigated, reports indicate that SonicWall SSL VPN devices are the primary target. It is crucial for organizations using the following SonicWall products to take immediate action:
- SonicWall firewalls with SSL VPN enabled
- SonicOS Gen 5 devices
How to Protect Your Organization
Given the active exploitation of this vulnerability, organizations using SonicWall firewalls should take the following steps to mitigate the risk:
- Apply Available Patches: Immediately apply any available security patches released by SonicWall. Monitor SonicWall's security advisories for updates.
- Enable Multi-Factor Authentication (MFA): Enforce MFA for all VPN and remote access connections to prevent unauthorized access.
- Review Firewall Configuration: Ensure that your firewall is configured according to security best practices. Disable any unnecessary services or ports.
- Monitor Network Traffic: Implement network monitoring tools to detect any suspicious activity or unauthorized access attempts.
- Implement a Robust Backup Strategy: Regularly back up your critical data to an offsite location to ensure business continuity in the event of a ransomware attack.
- Educate Employees: Train employees to recognize and report phishing emails and other social engineering attempts.
Key Takeaways
The Akira ransomware attack targeting SonicWall firewalls highlights the importance of proactive security measures and staying informed about emerging threats. By applying patches, enabling MFA, and implementing a robust security strategy, organizations can significantly reduce their risk of falling victim to ransomware attacks.
References
- The Hacker News: Akira Ransomware Exploits SonicWall VPNs in Likely Zero-Day Attack
- BleepingComputer: Surge of Akira Ransomware Attacks Hits SonicWall Firewall Devices
- Critical Path Security: Critical Alert: Akira Ransomware Surge Targets SonicWall Firewalls
- Cybersecurity Dive: Ransomware spike linked to potential zero-day flaw in SonicWall devices
- Arctic Wolf: Arctic Wolf Observes July 2025 Uptick in Akira Ransomware Activity Targeting SonicWall SSL VPN
- SonicWall Image




.jpg)